Prerequisites
IIS must be installed and working from the clients that will need the RootCA or certs signed by the RootCA server. See more for a simple IIS install guide here: https://scito.dk/2023/08/15/install-iis-for-certificate-authority-crl-and-root-certificate-distribution/
Steps
- Install Windows Server
- Fully Update Server
- Create C:\Windows\CAPolicy.inf
- Install ADCS Feature
- Setup ADCS
- Adjust settings in ADCS
- Copy the Cert and CRL to the web server
Step 1
Install a Windows server.
Step 2
Make sure the server is fully updated
Step 3
Create the file C:\Windows\CAPolicy.inf
With the following text. Remember to Change URLs under the following sections
- [InternalPolicy]
- [AuthorityInformationAccess]
- [CRLDistributionPoint]
If there are a specific internal OID being used, then change the OID to the company provided OID under the [InternalPolicy] Section
[Version]
Signature="$Windows NT$"
[PolicyStatementExtension]
Policies=InternalPolicy
[InternalPolicy]
OID= 1.2.3.4.1455.67.89.5
URL=http://win-root-ca/certs/cps.html
[Certsrv_Server]
RenewalKeyLength=4096
RenewalValidityPeriod=Years
RenewalValidityPeriodUnits=20
CRLPeriod=Years
CRLPeriodUnits=1
CRLDeltaPeriod=Days
CRLDeltaPeriodUnits=0
ClockSkewMinutes=20
LoadDefaultTemplates=True
AlternateSignatureAlgorithm=0
ForceUTF8=0
EnableKeyCounting=0
[AuthorityInformationAccess]
URL= http://Win-Root-CA01/certs/ScitoDK-RootCA.crt
URL= http://Win-Sub-CA01/certs/ScitoDK-RootCA.crt
URL=C:\Windows\System32\CertSrv\CertEnroll\ScitoDK-RootCA.crt
[CRLDistributionPoint]
URL= http://Win-Root-CA01/certs/ScitoDK-RootCA.crl
URL= http://Win-Sub-CA01/certs/ScitoDK-RootCA.crl
URL= C:\Windows\System32\CertSrv\CertEnroll\ScitoDK-RootCA.crl
[PolicyStatementExtension]
Policies = AllIssuancePolicy
Critical = FALSE
[AllIssuancePolicy]
OID = 2.5.29.32.0Step 4
Open Powershell and install the Windows Certificate Authority Feature
Add-WindowsFeature Adcs-Cert-Authority -IncludeManagementToolsStep 5
Open Powershell and configure the Windows Certificate Authority Feature.
Remember to Change the CACommonName.
Install-AdcsCertificationAuthority `
-OverwriteExistingKey `
-OverwriteExistingCAinDS `
-OverwriteExistingDatabase `
-CAType StandaloneRootCA `
-KeyLength 4096 `
-HashAlgorithm SHA256 `
-CryptoProviderName "RSA#Microsoft Software Key Storage Provider" `
-ValidityPeriod Years `
-ValidityPeriodUnits 20 `
-CACommonName "ScitoDK-RootCA" `
-ForceStep 6
Open Powershell for additional configuration of the Windows Certificate Authority Feature.
Remepber to change the URL for the Add-CACRLDistributionPoint and Add-CAAuthorityInformationAccess
If certutil failes when executed through powershell, then execute the certutil commands with a command prompt with administrative permissions.
$crllist = Get-CACrlDistributionPoint; foreach ($crl in $crllist) {Remove-CACrlDistributionPoint $crl.uri -Force};
Add-CACRLDistributionPoint -Uri C:\Windows\System32\CertSrv\CertEnroll\ScitoDK-RootCA.crl -PublishToServer -PublishDeltaToServer -Force
Add-CACRLDistributionPoint -Uri http://Win-Root-CA01/certs/ScitoDK-RootCA.crl -AddToCertificateCDP -AddToFreshestCrl -Force
Add-CACRLDistributionPoint -Uri http://Win-Sub-CA01/certs/ScitoDK-RootCA.crl -AddToCertificateCDP -AddToFreshestCrl -Force
Get-CAAuthorityInformationAccess | Remove-CAAuthorityInformationAccess -Force
Add-CAAuthorityInformationAccess -AddToCertificateAia http://Win-Sub-CA01/certs/ScitoDK-RootCA.crt -Force
Add-CAAuthorityInformationAccess -AddToCertificateAia http://Win-Root-CA01/certs/ScitoDK-RootCA.crt -Force
certutil.exe –setreg CA\CRLPeriodUnits 20
certutil.exe –setreg CA\CRLPeriod “Years”
certutil.exe –setreg CA\CRLOverlapPeriodUnits 3
certutil.exe –setreg CA\CRLOverlapPeriod “Weeks”
certutil.exe –setreg CA\ValidityPeriodUnits 10
certutil.exe –setreg CA\ValidityPeriod “Years”
certutil.exe -setreg CA\AuditFilter 127
Restart-Service certsvc
certutil -crlStep 7
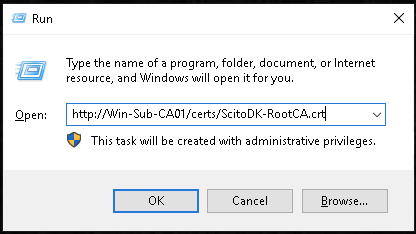
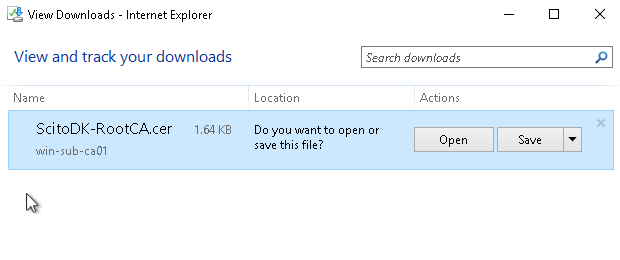
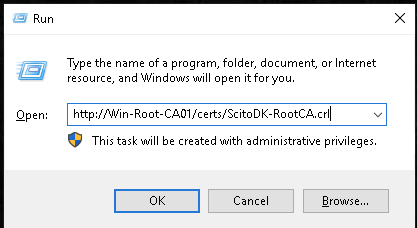
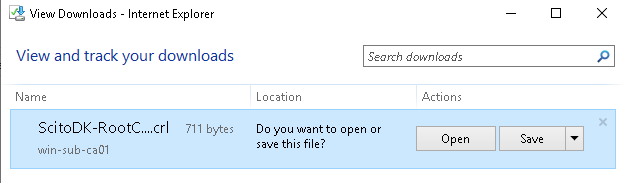
Copy the Root Certificat and the CRL file to the web site where the CRL are stated in the certificate
The files are located in the file directory under C:\Windows\System32\CertSrv\CertEnroll
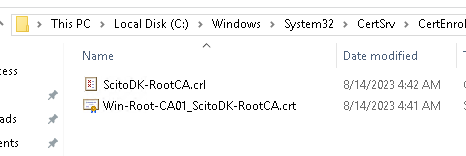
Remember to rename the Certificate file to the correct name stated in the CRL url. In this case it is ScitoDK-RootCA.crt
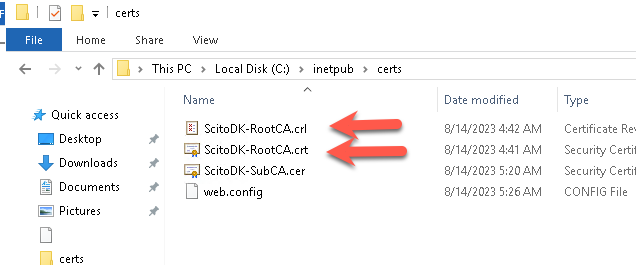
Test if the AIA is working: in this example it is http://Win-Sub-CA01/certs/ScitoDK-RootCA.crt.
Otherwise the clients or Subordinates CA will not work if the check to find the CRL file